Developer ‘Tiqs & Tricks
August 2023
Security & Secrets
Let’s review the Vantiq’s federated structure to remember how security is baked right into the Vantiq platform.
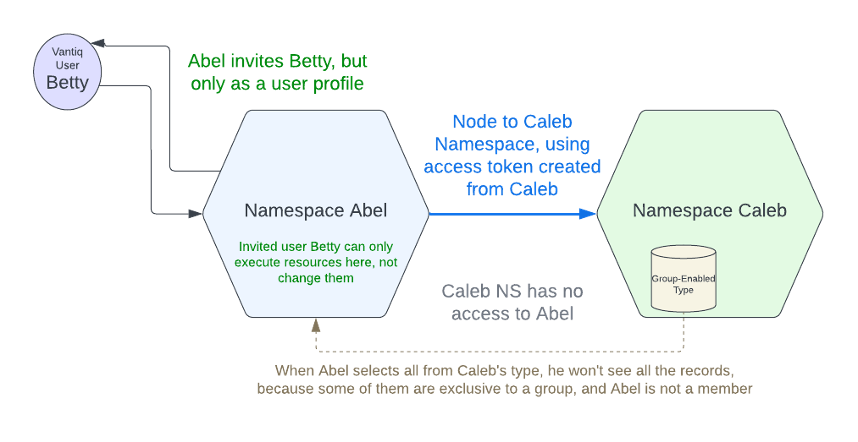
Namespaces are workspaces isolated to the Namespace Administrator/Developer. Only direct invitations from the Administrator make them accessible to other Vantiq developers, who may or may not be granted permission to make changes to the resources.
Nodes are connections between Namespaces. They require login credentials or an access token for the destination namespace, and they connect only in one direction. This Federation within Vantiq distributed systems ensures ease-of-use without sacrificing security.
Profiles contain capabilities for users to access Vantiq resources within Namespaces. They are most often set by default within the system, but the listed permissions can be altered by administrators with the proper authorization.
Groups are sets of users and access tokens with shared access to a collection of resources. Resource owners create the groups and designate membership.
All of these aspects of Vantiq federation and access control are well-documented in the Developer Guides. In this article, we’re going to spend a bit more time on a possibly lesser-known security feature in Vantiq: Secrets.
To understand the need for Secrets, ponder the following scenario: A coworker asks for access to your namespace to see a working example of a feature. You’re a team player, so you invite her in. Even if she’s only a “user” there, she can still see everything, including the API key to an expensive cloud service.
And sure enough, before long, your department is stuck with a big fat usage charge. Oh, the inhumanity!
Of course, if you’d stripped the project of the key and exported the file, this isn’t ideal either. The coworker will have to go through the hassle of creating a login and subscription just to see the use case running.
There is a better way to achieve the twin goals of information security and application usability: Vantiq Secrets. Let’s go over the steps I should have used to employ a Secret to secure my API key, while still being able to show a fully-running project to my coworker.
Step 1: Go to the Secrets pane from the Administer -> Advanced menu.
Step 2: Give the Secret a name and enter the sensitive information.
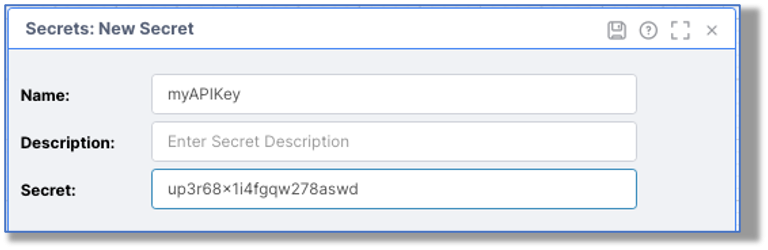
The Secret can be any text: an API key, password, etc. Once the Secret is set, the sensitive information cannot be retrieved again, but can be substituted for that information.
Step 3: Verify that the Secret is in the listing.

Step 4: Now use your Secret in the Source configuration.

And that’s all there is to it. Whomever you invite to the Namespace to see the running application cannot access the API key in the Remote source. If you export the project into a zip file, the Secret automatically disappears, so the key can’t even be misused in project copies.
Security is built into every part of the Vantiq platform. Secrets are a vital security feature within shared namespaces; they protect sensitive information without sacrificing usability. Make Secrets a part of your good development habits!
Developer ‘Tiqs & Tricks
August 2023
Security & Secrets
Let’s review the Vantiq’s federated structure to remember how security is baked right into the Vantiq platform.
Namespaces are workspaces isolated to the Namespace Administrator/Developer. Only direct invitations from the Administrator make them accessible to other Vantiq developers, who may or may not be granted permission to make changes to the resources.
Nodes are connections between Namespaces. They require login credentials or an access token for the destination namespace, and they connect only in one direction. This Federation within Vantiq distributed systems ensures ease-of-use without sacrificing security.
Profiles contain capabilities for users to access Vantiq resources within Namespaces. They are most often set by default within the system, but the listed permissions can be altered by administrators with the proper authorization.
Groups are sets of users and access tokens with shared access to a collection of resources. Resource owners create the groups and designate membership.
All of these aspects of Vantiq federation and access control are well-documented in the Developer Guides. In this article, we’re going to spend a bit more time on a possibly lesser-known security feature in Vantiq: Secrets.
To understand the need for Secrets, ponder the following scenario: A coworker asks for access to your namespace to see a working example of a feature. You’re a team player, so you invite her in. Even if she’s only a “user” there, she can still see everything, including the API key to an expensive cloud service.
And sure enough, before long, your department is stuck with a big fat usage charge. Oh, the inhumanity!
Of course, if you’d stripped the project of the key and exported the file, this isn’t ideal either. The coworker will have to go through the hassle of creating a login and subscription just to see the use case running.
There is a better way to achieve the twin goals of information security and application usability: Vantiq Secrets. Let’s go over the steps I should have used to employ a Secret to secure my API key, while still being able to show a fully-running project to my coworker.
Step 1: Go to the Secrets pane from the Administer -> Advanced menu.
Step 2: Give the Secret a name and enter the sensitive information.
The Secret can be any text: an API key, password, etc. Once the Secret is set, the sensitive information cannot be retrieved again, but can be substituted for that information.
Step 3: Verify that the Secret is in the listing.
Step 4: Now use your Secret in the Source configuration.
And that’s all there is to it. Whomever you invite to the Namespace to see the running application cannot access the API key in the Remote source. If you export the project into a zip file, the Secret automatically disappears, so the key can’t even be misused in project copies.
Security is built into every part of the Vantiq platform. Secrets are a vital security feature within shared namespaces; they protect sensitive information without sacrificing usability. Make Secrets a part of your good development habits!